Description
Introduction
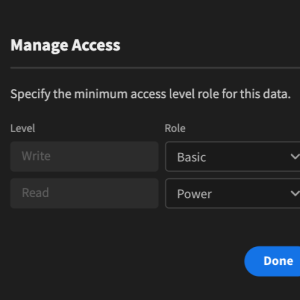
Audit log settings files configure the logging of security-related events, ensuring that all actions within an application are monitored for suspicious activities. These logs help with security analysis and compliance reporting.
Problems It Solves
– Identifies unauthorized access attempts
– Tracks changes to user permissions and security settings
– Helps in forensic analysis of security incidents
– Ensures compliance with industry regulations (e.g., PCI-DSS, SOC 2)
– Improves accountability by logging all sensitive actions
– Reduces risk of insider threats by monitoring user activities
About Code Format
These files are typically stored in JSON, CSV, or log file formats, capturing timestamps, user actions, IP addresses, and event descriptions.
Customization
– Define log retention policies based on compliance needs
– Adjust log verbosity for detailed or summarized records
– Implement real-time alerts for critical security events
– Enable encryption for stored audit logs
– Integrate with SIEM (Security Information and Event Management) systems
– Configure separate logs for different security categories


Juliana –
“As a solo developer, incorporating robust audit logging seemed daunting until I found this tool. Setting up the “Audit Log Settings” was surprisingly straightforward, and the features are exactly what I needed: comprehensive tracking of security events, monitoring login attempts, and clear records of unauthorized access. It’s been instrumental in bolstering my application’s security posture, ensuring regulatory compliance, and providing invaluable data for forensic analysis. This utility has significantly improved my application’s security and my peace of mind – it’s a brilliant solution.”
Mathias –
“As a solo developer, incorporating audit logging seemed daunting until I found this. The clearly defined settings for tracking security events, monitoring access, and recording unauthorized attempts were exactly what I needed. It simplifies compliance and gives me peace of mind knowing I have timestamped logs for accountability and potential forensic analysis. A must-have tool for any security-conscious individual developer!”
Dalhatu –
“This tool is fantastic for a solo developer like myself. Implementing audit logging always felt daunting, but this made it surprisingly straightforward. The functionality to track security events, login attempts, and access changes, especially unauthorized access, is invaluable. It really simplifies ensuring compliance and knowing I have detailed, timestamped logs for potential forensic analysis provides immense peace of mind and improves accountability in my application development.”
Monsurat –
“As a solo developer, this Audit Log Settings addition has been invaluable for bolstering my application’s security. It provides a clear and comprehensive record of all critical events, from login attempts to unauthorized access, making compliance and forensic analysis significantly simpler. The timestamped logs have substantially improved accountability, giving me peace of mind knowing that I have a robust system in place to track and analyze security-related activities.”