Description
Introduction
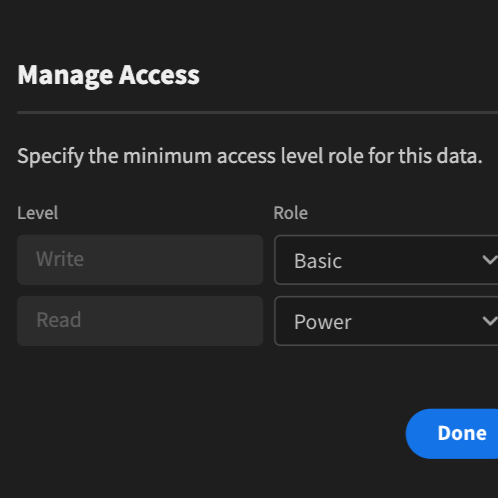
Access control rule files define user permissions, ensuring that only authorized individuals can access specific resources within an application. These files are essential for implementing Role-Based Access Control (RBAC) and ensuring data security.
Problems It Solves
– Prevents unauthorized access to sensitive data
– Reduces risks of data leaks by defining clear permissions
– Enhances compliance with security standards (e.g., GDPR, HIPAA)
– Simplifies permission management across different user roles
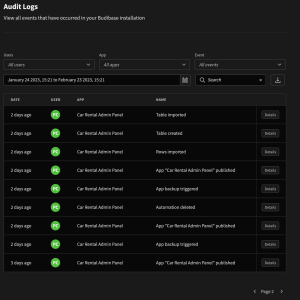
– Supports logging of access attempts for security monitoring
– Prevents privilege escalation by restricting admin actions
About Code Format
These files are often stored in JSON, YAML, or database configurations, defining user roles, access levels, and permission scopes.
Customization
– Define different permission levels for users and admins
– Adjust access rules dynamically based on business needs
– Implement time-based access restrictions for sensitive actions
– Set up permission inheritance for efficiency
– Integrate logging mechanisms for auditing user actions
– Configure temporary access permissions for external users


Ajayi –
“This access control solution has been a real boon to my solo development efforts. It simplified the complex task of managing user permissions and restrictions, allowing me to prevent unauthorized data access effectively. The dynamic permission updates are incredibly helpful, and the access logging provides valuable insights for auditing. It’s significantly improved my application’s security and compliance, giving me peace of mind.”
Ahmed –
“This access control addition has been a tremendous help in my solo development efforts. It streamlines the process of managing user permissions and security. The ability to dynamically update permissions and the built-in access logging features are invaluable for ensuring compliance and preventing unauthorized data access. It’s significantly improved the security and control of my application.”
Kikelomo –
“This access control functionality has been invaluable in securing my application. As a solo developer, managing permissions and restrictions was a significant challenge. This tool made it straightforward to define roles, prevent unauthorized access, and keep an audit trail, ultimately enhancing my app’s security posture and simplifying compliance requirements. It’s a must-have for any developer looking to build secure and reliable applications.”